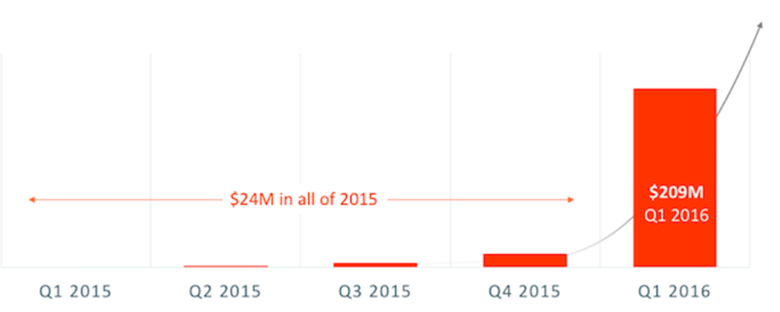
According to the FBI, ransomware attacks have increased 35-fold during 2016 resulting in an estimated US$209 million paid out every quarter. No one is immune, with attacks impacting hospitals, schools, government, law enforcement agencies and businesses of all sizes. The increased frequency of attacks has organisations thinking differently about their approach to ransomware, writes CTERA’s Jeff Denworth.
[easy-tweet tweet=”Increased frequency of attacks has organisations thinking differently about their approach to ransomware” hashtags=”tech, security”]
Ransomware has reached the heights of a global IT epidemic that every organisation has either already faced – about 50% of organisations have been breached – or will almost certainly face as the pace of cyber-attacks increases on a daily basis. The costs are spiraling with ransomware payments being made via anonymous bitcoin transactions – where it can cost anywhere from $500-$2,000 to unlock an average PC. The anonymity makes it’s difficult to know precisely how many anonymous payments have been paid to cyber-criminals.
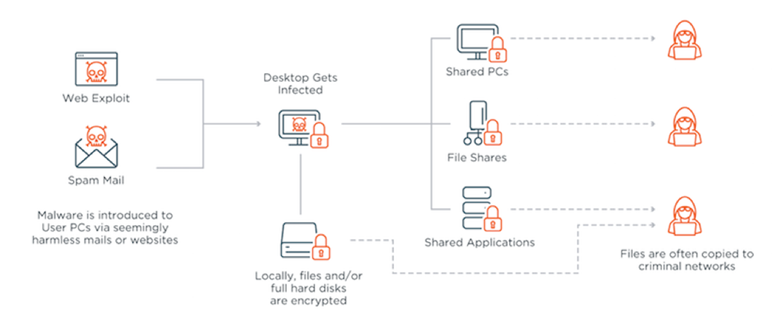
Here’s a look at how it works:
What we are seeing is an exponential spike in ransomware activity that is seeing it look likely to become a US$1bn business this year. Compounding this is that success of ransomware encourages cyber criminals to introduce new strains of malware and increase their efforts.
Take a look:
Two especially nasty tweaks to ransomware are starting to emerge:
- Certain cyber-criminals are capturing data that ransomware can copy out of your network for the purposes of selling it to interested third parties, enabling industrial espionage.
- There have been reports of cases where customers have paid ransomware attackers and then never receive encryption keys for decrypting their PCs in return.
The problem then is substantial and getting larger so now is the time to start fighting back and putting countermeasures in place.
Countermeasures to fight back against crypto-malware:
Step #1. Secure your perimeter to minimise the chance of breach:
- Patch your operating systems and keep your operating systems up to date.
- Train employees on ransomware and their role in protecting the organisation’s data.
- Disable macro scripts from office files transmitted over email.
- Limit access to critical and rapidly changing datasets to only need-to-know users.
Step #2. Back up all files and systems to avoid paying ransom to recover from crypto events.
- Backup your endpoints, back up your file servers.
- Implement lightweight optimised data protection tools that minimise recovery points.
For the last 20 years, the market has been conditioned for daily backups. Whether we’re talking server or endpoint backup, in both cases file storage systems have been built for relatively lax backup intervals because backups have been expensive, requiring lots of CPU, lots of storage and too much time, and organisations haven’t had to deal with an explosion of file-locking malware attacks.
The use of legacy backup software in an organisation becomes a major issue for organisations where knowledge workers are continuously storing data on PCs and file shares. For example, an organisation that has 1,000 knowledge worker employees with file access by power users and IT teams has all of its files shares vulnerable. Daily backup using legacy tools leaves 24 hours of work unprotected which equates to 2.73 many years of cumulative lost productivity.
That demonstrates how legacy backup tools can have real costs for organisations that are routinely faced with crypto-ransomware. Modern backup solutions, including CTERA’s, can enable organisations to achieve a finer degree of backup interval granularity through the use of global, source-based deduplication, incremental-ever versioning and the ability to track file changes without doing full system scans. That said – default settings for even the most efficient tools are anywhere from four to eight hours, which is nearly a full business day. Therefore, the same problem could essentially persist.
In spite of the relatively large recovery point, data protection tools – or backup – will always play an instrumental role as a ransomware countermeasure, in large part because of backup software’s ability to recover full systems and system profiles. The Petya virus, for example, forgoes single file encryption and will simply lock up a full desktop hard disk. These type of viruses create the need for simple tools that can help with full PC restores and backup software fits the bill.
The lines of data protection are becoming increasingly blurred between NAS and Backup Software as Enterprise File Sync and Share, a self-protecting file management and collaboration tool that provides user-level storage and file recovery tools, emerges into the market. These tools create incremental versions of files as they are changed and updated, and are protected on an “event basis” (a file save) as opposed to a ‘scheduled’ basis (a pre-defined backup interval).
[easy-tweet tweet=”The lines of data protection are becoming increasingly blurred” hashtags=”tech, cloud, security”]
The result of an ‘event-based’ data protection agenda is much more compelling than a scheduled backup strategy that protects user data in 24, 12, six or even one-hour intervals.
Philosophically backup everything
The FBI is right to advise that you back up your systems. You’ll want to recover desktops and servers without Herculean recovery efforts, and modern backup tools can make it simple to protect systems and easy to recover full profiles.
CTERA Enterprise File Sync and Share and Sync Cloud Storage Gateway models can publish and version file updates with less than five minutes. In the event of a ransomware attack, you can roll recover your desktop with CTERA backup software and then recover to versions of folders that were stored in CTERA Sync products to ensure you are recovering to the most recent file state.
CTERA and our customers have been fortunate to catch and recover from some very serious ransomware crypto-lock events. Using very granular file sync and backup procedures, CTERA customers have minimised their recovery points to as little as five minutes – in comparison to 24 hours or more with competing technology. With the right data protection tools, they’ve successfully saved themselves from paying hundreds of thousands of pounds in ransom and minimised the period of business outage.
[easy-tweet tweet=”The FBI is right to advise that you back up your systems.” hashtags=”tech, cloud, ransomeware”]
The only way we can put an end to this epidemic is by building the right safeguards that eliminate enterprise vulnerability and end the need to pay cyber-criminals to access our data and our systems. Whether you choose CTERA tools or any number of other approaches to safeguarding your organisation, choose to be prepared and please do it right now.
Jeff Denworth, SVP Marketing, CTERA