In the past week yet another corporate brand has been hacked impacting up to 70 million users. Red faced by the original email attack in 2012, Dropbox has had to release another statement to users to reset their passwords.
[easy-tweet tweet=”Dropbox has had to release another statement to users to reset their passwords” hashtags=”security, tech, cloud”]
In reality, this is not only a consumer but also a corporate security issue. Today we are using more and more cloud based services that morph into our daily lives. Personal and business accounts are becoming more bimodal (i.e. having two sets or modes of operation within IT) to keep up with business and digital transformation change.
Right now the best way for organisations to support this mode is to consider how a leakage can be stopped even before it is compromised. DLP (Data Leakage Protection) is paramount in today’s 24/7 world.
Some companies are finding it difficult to manage data protection and security on their own as there are so many paths to protect (i.e. monitoring, encrypting, filtering, blocking sensitive information kept at rest or in motion within the managed IT environment from perimeter to end point devices).
Realistically, considering the following is just a start to developing and maintaining security:
- Stopping the stupid – 73 percent of IT leakage is due to accidents or stupidity, according to data from InfoWatch (e.g. Laptops or USB keys lost or left, people sharing valuable data via email or even via personal file sharing sites).
- Putting in place the correct endpoint security protection.
- Training, training and re-training on ways to ‘stop the stupid‘ and the risks to brand damage.
- Enhancing web gateway protection.
- Update Network Access Control (NAC) regularly – ensuring only company based devices are connected to the network and compliant with the organisation’s security policy.
- Build in end user analytics tools that can determine abnormal behaviour.
Data leakage is definitely on the upward trend where more personal data leaks are occurring. Reported leaks globally in 2015 by InfoWatch were an astonishing 1500 and counting. This is a staggering 61 percent increase since 2012 when the alleged Dropbox attack occurred.
Certain industries are targeted higher than others by external intruders such as high tech, manufacturing and retail versus Local Government. Surprisingly, healthcare is the only sector where insider leaks are the highest.
This could be for a variety of reasons including mistrust of drug and medicine companies, including overcharging, which soon gathers momentum on social media. Mylan Inc has already seen brand impact with their share price dropping over 4 percent since last week with their price increase for EpiPens in the US.
To put into perspective the impact on data leaks, last year alone saw at least 21 mega leaks which resulted in the loss of over 10 million records per brand.
Organisations need to focus their efforts on containment, risk aversion and brand damage limitation. It’s the PR nightmare that most CxO’s in any organisation dread and result in sleepless nights. Today, reputational brand damage is shared on social channels way before the organisation’s PR team can make a publicity statement. Consider the Co-Op scandal of 2014 where salary data was leaked. This caused the CEO to resign and comment that it was unable to adopt professional and commercial governance. No-one recalls the CEO and his team rescuing the banking arm of the business from its largest crisis in its 150 year history.
[easy-tweet tweet=”Organisations need to focus their efforts on containment, risk aversion and brand damage limitation.” hashtags=”tech, security, cloud”]
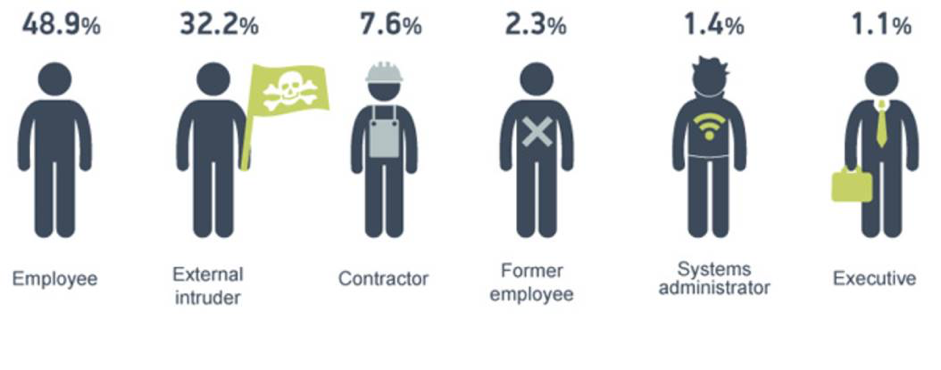
Originators of leaks vary but on the whole come from existing employees, Senior Execs and IT departments System Administrators (1.4 percent) (see diagram below). Each leakage is not dissimilar and often occurs through malice or an inability to keep company data secure. In 2015 alone nearly 8 percent of the overall leaks were caused by access rights abuse, manipulation of data or data leaked on a “need to know basis”, according to InfoWatch’s 2015 Data Leakage report. Leakage of Twitter’s quarterly update plunged shares by at least 18% in a single day and took some months to recover.
Source of diagram: Data Leakage Report 2015, InfoWatch
In summary, consider the points above and never re-use passwords (especially personal and business ones). Brand damage can be very severe to an organisation, you only have to look at the financial impact reported on TalkTalk last year.
Mark Read-Jones, Strategy Director, Timico Technology Services, a global Managed Service Cloud Provider
Mark is a highly effective Senior Outsourcing and Consultancy specialist with over 15 years’ experience within business. He fosters deep and enduring relationships with clients, colleagues and partners up to CXO level. Mark is an exceptional leader, who drives change and the adoption of emerging services and technologies within new and existing clients. Mark maps business issues to strategic road maps that create business advantage and return on investment (ROI) for an organisation; whether locally or internationally through people, process or technology.




Comments are closed.