The irresistible shift to cloud infrastructure has been accompanied by a certain amount of fear and uncertainty. Part of the reluctance has been a sense of “who is minding the shop” and a concern over the lack of visibility and control. In one sense, cloud data centre infrastructure is potentially more secure than private infrastructure, as it may be maintained by a large, specialised team with potentially greater expertise that can attend to security issues that arise. In another, the cloud opens up several new attack surfaces that could be used by cybercriminals and other bad actors.
[easy-tweet tweet=”The shift to #cloud infrastructure has been accompanied by a fear of uncertainty” hashtags=”tech, IT”]
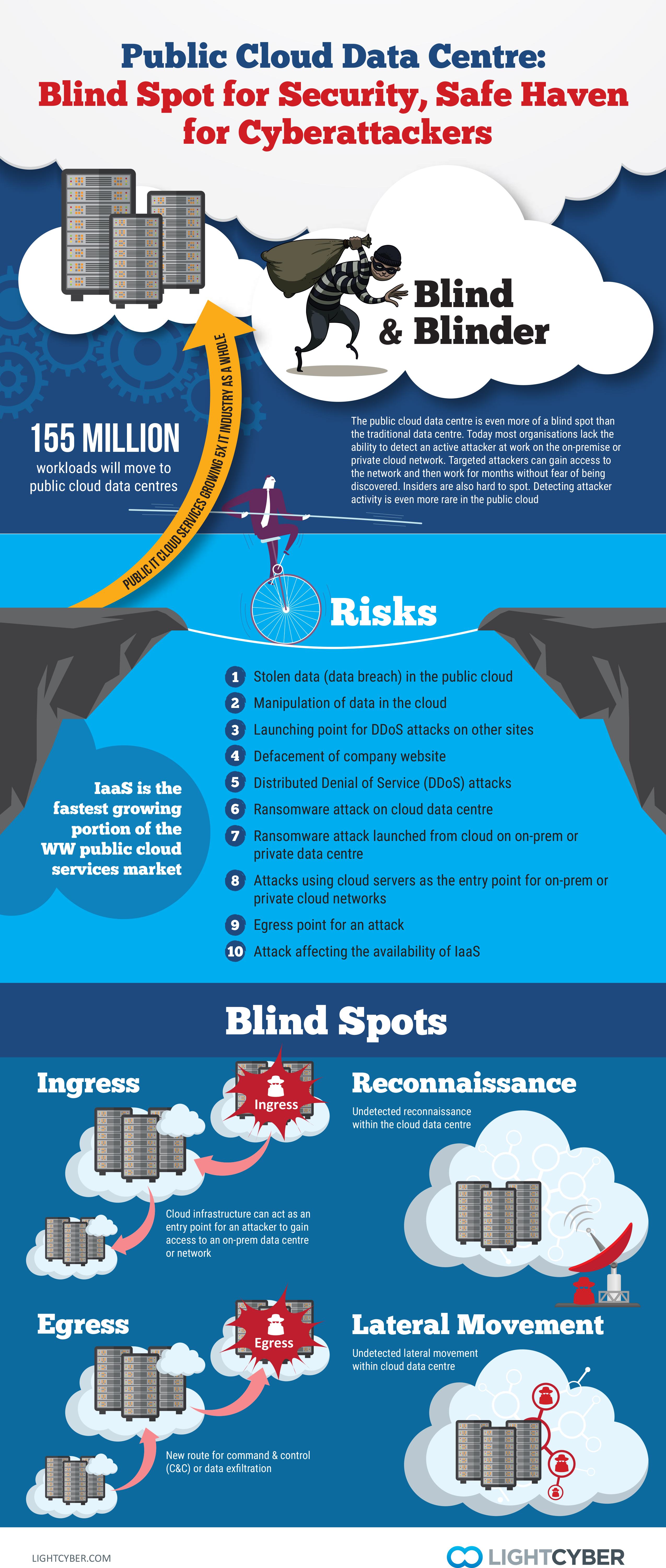
Most organisations already face a serious security deficit. Few can detect an active attacker at work on their network. The industry average dwell time of some five weeks reflects the failure of traditional security to find an intruder that has circumvented preventative security and is working towards a data breach. Companies should first address the problem they face on-premises and then address the blind spots in the cloud. Both are important steps to safeguard data and resources.
The public cloud data centre can be a new ingress or egress point for attackers to gain a foothold into one’s network or as a channel for command and control communications and data exfiltration. In addition, the reconnaissance and lateral movement that an attacker must employ once they gain access can be done without fear of discovery. These four types of operational activities must be detected and stopped, if organisations want to protect their assets from attackers.
Closing all the gaps is important in the drive to protect networks from a data breach. Attackers are agile, and if one tactic is too difficult or not possible, they can easily move to plan B. For some companies, this may mean that an attacker would turn to the cloud data centre to help accomplish their goals. If attackers can use a public cloud data centre for undetected ingress and egress, it invalidates some of the efforts an organisation has put in place to protect their own network.
[easy-tweet tweet=”An attacker could turn to the cloud data centre to help accomplish their goals.” hashtags=”hacking, tech, cloud”]
Often, a development or test instance becomes the Achilles heel in the cloud. Many of these development or test instances may have been intended for a specific purpose at a specific point in time, but they can become forgotten and left up —a perfect entry-way for an attacker. One of these forgotten instances could be the easy route an attacker utilises.
Finding active attackers in on-premises networks can be accomplished by identifying their operational activities as they probe servers and misuse credentials. Having a complete vantage to network traffic is essential, as the primary attack activities involve reconnaissance and lateral movement—things that happen on a network, between devices. Discerning these comes through behavioural profiling of all users and devices. Once a baseline of learned good behaviour is obtained, it is possible to detect anomalies. These anomalies need further refinement to find those that are truly indicative of an attack.
Combining full network visibility with machine learning allows organisations to detect an attacker that might otherwise be invisible to the security team. Unfortunately, gaining access to a mechanism for visibility in the cloud has not existed until recently. Now, organisations can take advantage of Behavioural Attack Detection in the cloud and use native Amazon Web Service VPC Flow Logs or the new Gigamon Visibility Fabric for AWS to monitor their virtual network. They can also protect hybrid cloud environments, monitoring user access to cloud servers and detecting anomalous activity indicative of an attack.
[easy-tweet tweet=”Organisations can take advantage of Behavioural Attack Detection in the cloud” hashtags=”tech, cloud, IT”]
The cost and consequences of a data breach are rapidly climbing, particularly with the enforcement of the EU General Data Protection Regulation (GDPR) which applies to companies in the EU or doing business in the EU. Besides hefty penalties, damage to brand and reputation or loss of intellectual property or business secrets could put a company out of business. While it is nearly impossible to ensure that no endpoint will ever get compromised, it is possible to find active attacks quickly and prevent a simple malware infection from turning into a costly data breach. Closing all the blind spots for attackers to operate in without notice is essential to make this a reality.
Kasey Cross, Product Marketing Manager at LightCyber