Data security is an extremely hot topic at present.
Securing laptops and mobile devices is not only essential but also presents management complexities due to the very mobile nature of the devices that make them so very appealing in the first place.
Making the situation that much worse is that loss of sensitive data can destroy a company’s reputation with its customers overnight, as well as the public at large. Who would want to trust a company with data again when they have proven they cannot look after the data they already possess?
Whilst it is best practice to educate staff in good data hygiene and data loss prevention, it is the company that must take the steps necessary to secure the data, being ultimately responsible in the eyes of the law.
No matter how much businesses plan for it, data loss, or more accurately, loss of control of the data and devices will still occur through accidental loss, theft and other nefarious means, no matter how much businesses plan for it.
A typical scenario, back before data encryption entered the consciousness of most administrators; a salesperson within the organisation left their laptop in their car in clear view, rushing to
a client meeting. Upon returning, he was greeted with a smashed window and a missing laptop. Hence, administrators often need to protect the company from the users.
While for most companies that may have been the end of the story, the laptop in question had remote viewing and management capabilities installed. It was interesting and horrifying at the same time to see the eventual owner of the laptop rifle through the documents, price lists, customer details and other commercially sensitive data. In the hands of a competitor, it could have had a devastating effect. The lesson learnt for the company’s system administrators was that full drive encryption was not an option, but a necessity.
Loss and theft also occur in other ways.
“Across Transport for London’s (TfL) network alone last year an average of three laptops went missing every day*”,
says Tony Hollingsbee, SSD Business Manager for Kingston Technology. “This obviously exposes organisations to
significant risks such as reputational damage, loss of trust or fines, if there were personal data on the laptop.”
Furthermore, not all staff can be trusted, and devices can be stolen for personal profit or gain. Encrypting the drives also means that any failures on it that need to be returned to the manufacturer are encrypted.
For today’s administrators the management overhead of drive encryption and its associated security has become much easier to manage and implement on a technical level but understanding how to put the solution into practice correctly is essential. It is not just a technical matter but a business process that needs to be adequately evaluated and introduced properly.
The differentiator is how a business plans for data loss and responds to it that makes you a data security winner or a data security loser.
Adopting a strong, well-managed encryption solution can make the difference between a simple device loss report to the appropriate authorities and reputational destruction. Moreover, the stakes have just been significantly increased with the introduction of GDPR (General Data Protection Regulation).
As part of the GDPR legislation, there is a requirement to provide a reasonable level of protection for data concerning third parties against data loss or theft. Failure to do so can come with large financial penalties, up to four per cent of global turnover.
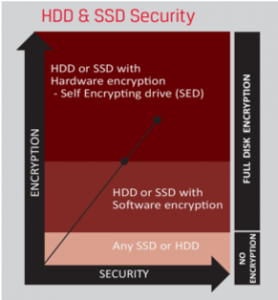
Mobile security is but one aspect of GDPR. Here we look at the requirements, background and practicalities of implementing secure data encryption. There are many types of data encryption, but without doubt, Full Disk Encryption is both more secure and easy to manage.
Historically, the downside of full drive encryption was the not insignificant performance degradation it caused, magnified many times over on low-end hardware. Whilst improvements in CPUs and architecture helped negate some of the impacts, there was still a performance hit.
Stuart is a Fortune 500 administrator and classed as a vExpert specialising in large scale virtualization and infrastructure management. Amongst his skill sets are Linux and Windows administration. In a past life, he was responsible for systems and security, ranging from small companies to government agencies. When not managing infrastructure he can be found experimenting with new forms of technology.