46Data Classification, Security Frameworks and International Standards
All of a sudden, everywhere you look, the cloud is the new normal. Top service providers’ cloud revenues are doubling year on year at the start of what is predicted to be a sustained period of growth in cloud services. As IT workloads have migrated to the cloud, the private sector has led the charge. Governments have been towards the rear, with cloud spend to date generally accounting for less than five percent of a given country’s public sector IT budget. This looks likely to increase quickly as the public sector starts to overcome the blockers to cloud uptake.
[easy-tweet tweet=”All of a sudden, everywhere you look, the cloud is the new normal.” user=”KempITLaw” usehashtags=”no”]
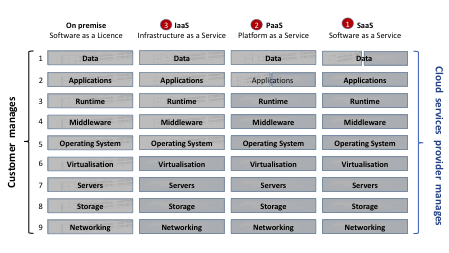
The classic NIST definition of the Cloud specifies Software (SaaS), Platform (PaaS) and Infrastructure (IaaS) as the main Cloud services (see figure 1 below), where each is supplied via network access on a self-service, on-demand, one-to-many, scalable and metered basis, from a private (dedicated), community (group), public (multi-tenant) or hybrid (load balancing) Cloud data centre.
The benefits of the Cloud are real and evidenced
The benefits of the Cloud are real and evidenced, especially between the private and public cloud where public cloud economies of scale, demand diversification and multi-tenancy are estimated to drive down the costs of an equivalent private cloud by up to ninety percent.
Equally real also are the blockers to public sector cloud adoption, where studies consistently show that management of security risk is at the centre of practical, front-line worries about cloud take-up, and that removing them will be indispensable to unlocking the potential for growth. Demonstrating effective management of cloud security to and for all stakeholders is therefore central to cloud adoption by the public sector and a key driver of government cloud policy.
Figure 1: Software as a Licence to Software as a Service: the Cloud Service Model Continuum
A number of governments have been at the forefront of developing an effective approach to cloud security management, especially the UK which has published a full suite of documentation covering the essentials. The key elements for effective cloud security management have emerged as:
- a structured and transparent approach to data classification;
- a transparent and published cloud security framework based on the data classification; and
- the use of international standards as an effective way to demonstrate compliance with the cloud security framework.
Data classification is the real key to unlocking the cloud. This allows organisations to categorise the data they possess by sensitivity and business impact in order to assess risk. The UK has recently moved to a three tier classification model (OFFICIAL → SECRET → TOP SECRET) and has indicated that the OFFICIAL category ‘covers up to ninety percent of public sector business’ like most policy development, service delivery, legal advice, personal data, contracts, statistics, case files, and administrative data. OFFICIAL data in the UK ‘must be secured against a threat model that is broadly similar to that faced by a large UK private company’ with levels of security controls that ‘are based on good, commercially available products in the same way that the best-run businesses manage their sensitive information’.
[easy-tweet tweet=”Data classification is the real key to unlocking the cloud” user=”KempITLaw” usehashtags=”no”]
Data classification enables a cloud security framework to be developed and mapped to the different kinds of data. Here, the UK government has published a full set of cloud security principles, guidance and implementation[i] dealing with the range of relevant issues from data in transit protection through to security of supply chain, personnel, service operations and consumer management. These cloud security principles have been taken up by the supplier community, and tier one providers like Amazon and Microsoft have published documentation based on them in order to assist UK public sector customers in making cloud service buying decisions consistently with the mandated requirements.
Compliance with the published security framework, in turn based on the data classification, can then be evidenced through procedures designed to assess and certify achievement of the cloud security standards. The UK’s cloud security guidance on standards references ISO 27001 as a standard to assess implementation of its cloud security principles. ISO 27001 sets out for managing information security certain control objectives and the controls themselves against which an organisation can be certified, audited and benchmarked. Organisations can request third party certification assurance and this certification can then be provided to the organisation’s customers. ISO 27001 certification is generally expected for approved providers of UK G-Cloud services.
This pragmatic but comprehensive combination of data classification and cloud security framework with the assurance that evidenced compliance with generally accepted international standards provides will go a long way to unlocking the benefits, removing the blockers and enabling the public sector cloud around the world to achieve its potential.
If you would like to see further information on this topic, please see our October 2015 white papers on Seeding the Global Public Sector Cloud, Part I – A Role for International Standards and Part II – The UK’s Approach as Pathfinder for Other Countries.
Richard Kemp, Founder, Kemp IT Law
Richard Kemp, founder of Kemp IT Law is widely recognised as one of the world’s top IT lawyers with over thirty years’ experience at the leading edge of technology law practice. He has built an outstanding reputation for advice that combines commerciality and client service with innovative legal solutions to the business challenges of technology development, deployment and regulation.